【WP】XCTF-*CTFpwn题
examination
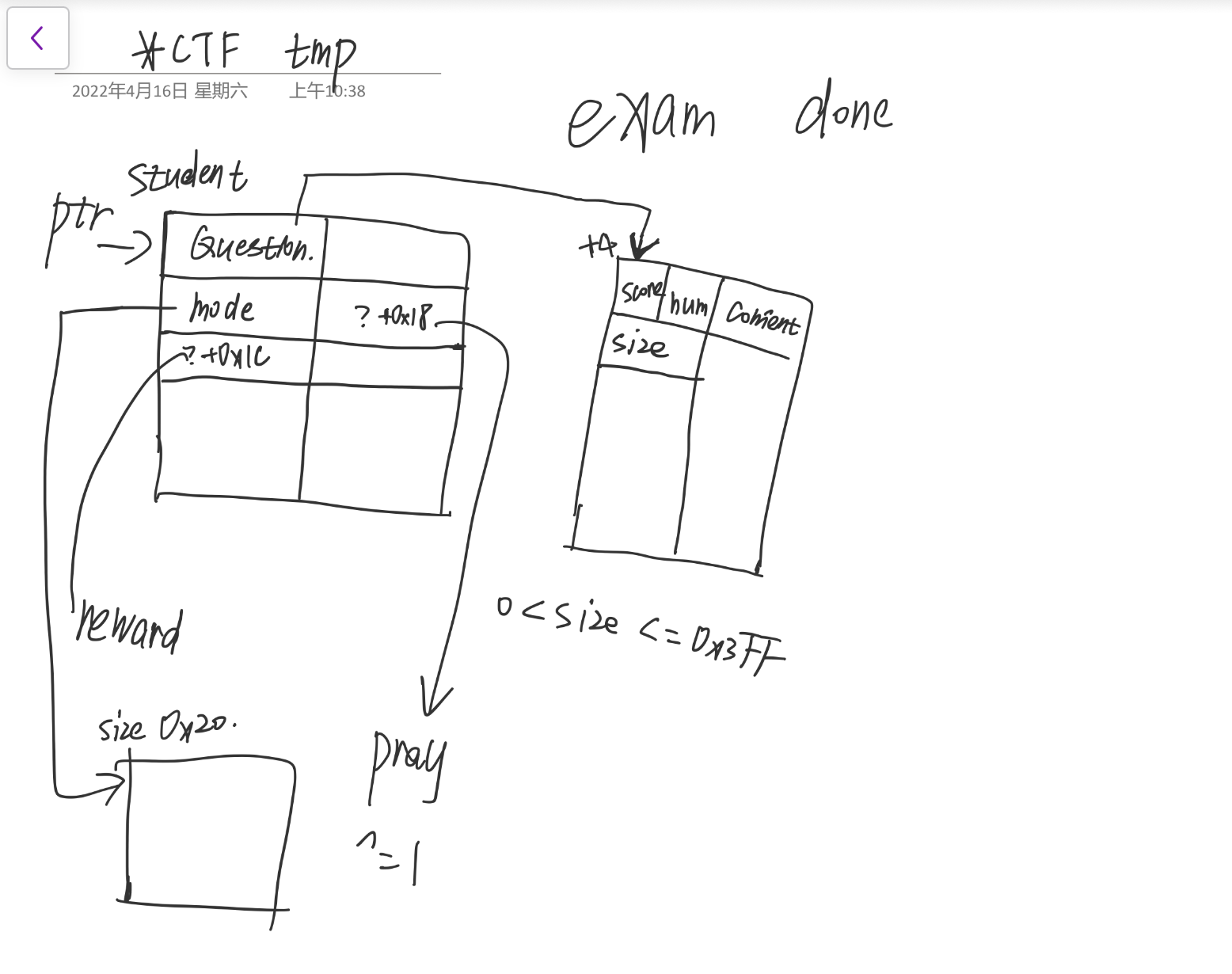
question num设1,score打出负数,unsigned变大数,check review得到堆地址和任意地址加一(没用上)
set mode功能能改指针最后一个字节,范围0x0~0x64
可以造成堆上局部的任意写
做法如下:
先打score负数,check review得到堆地址
布置一下堆,利用setmode中局部的任意写改mode指针,再写入内容修改size,释放掉,造出unsorted bin
接着把基址申请到comment上,再读出来即得到基址
再往下构造,最终利用局部的任意写控制mode指针改student结构体,控制question指向自己,content指向__malloc_hook,size写个数进去,从而构造出真正的任意写,再用写comment把one gadget写到__malloc_hook,调用teacher的隐藏选项触发malloc即可
结构
exp
1 | from pwn import* |
babynote
musl1.2.2的题
半年前学了一下之后就没碰过了,所以熟练度比较低做到了半夜
题目本身比较简单,delete链表中最后一个,也即最早插入的节点时没有卸下,存在uaf
首先构造,content也申请0x28的大小和结构体放到一块group中,构造一个结构体在group最下面,content在上面,然后再释放掉,再让结构体拿到本来content的内容,从而泄露出结构体内的指针,也即拿到基址
接着利用uaf发现next指针指到某块content上,也即节点可控
利用可控节点再链入一个节点,伪造两个节点
前者用来泄露secret
后者用来构造一个fake chunk,指向fake group,fake group又指向fake meta,fake meta的prev指向ofl_head-8,next指向可控的堆上
释放fake chunk,trigger dequeue(),其中m->prev->next = m->next;使得ofl_head写入可控堆地址
最后构造一下fake _IO_FILE,劫持write指针,栈迁移到堆上执行execve("/bin/sh",0,0)
exp
远程和本地的fake meta地址不太一样,不过确定的是距离libc基址偏移n页,可以利用最后伪造的节点打印出来验证
1 | from pwn import * |
babyarm
arm架构的内核题,复现一手
记录一下调试过程
断点下到device_read中的copy_to_user和device_write中
运行,首先断在
1 | read(fd, buf, 0xe0); |
1 | # device_read |
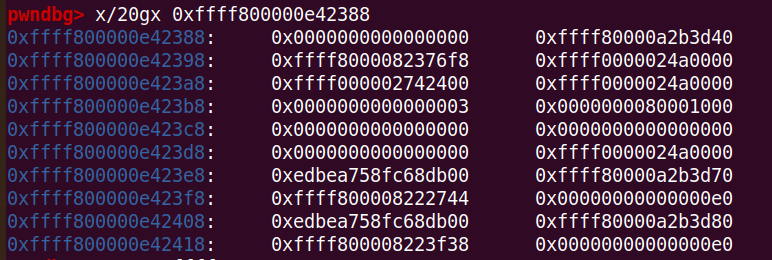
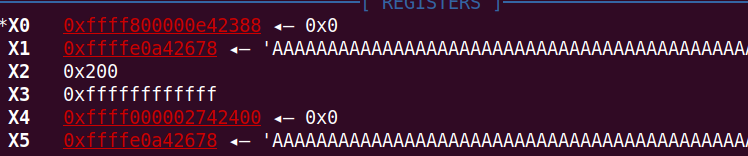
X0指向v15,X1指向demo_buf,X2代表length,v15其实就是user态传进来的地址。所以会把tmp的内容复制到v15中。tmp原本是一个device_read函数的局部变量,所以这样一来就把栈的很多信息拿到了,其中包括canary。
接着走到device_write中的copy_from_user
看到地址就是刚才read读进来的栈地址,且由于其距离栈底0x88,所以可以栈溢出了。存在canary,但上一步read已经泄露得到了canary。
然后是rop,由于题目没有开启什么保护,地址是固定的,执行commit_cred(prepare_kernel_cred(0))提权
最后要用gadget返回到用户态
先这样吧,不完全懂……